In our previous chapter we talked about how to reach our EC2 instance into the public VPC and all the different components that are involved in that communication.
But let’s complicate things a little bit more. What happens if our components are on the Private Network without access to the internet?
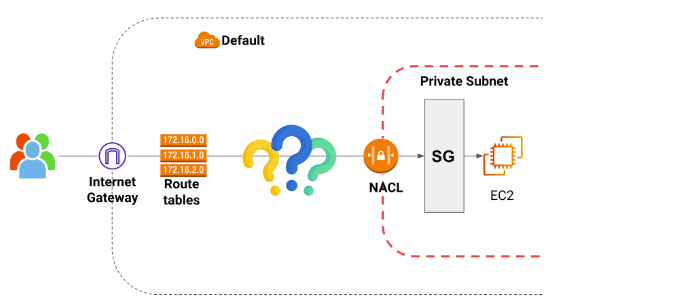
When we look at this picture we recognise many of the components that are involved in the flow, but something is missing.
So what is the magic behind it?
Well, let’s introduce the Bastion Host concept.
Bastion Host
A bastion host is a server whose purpose is to provide access to a private network from an external network, such as the Internet. Because of its exposure to potential attacks, a bastion host must minimize the chances of penetration.
They typically run a minimum amount of services in order to reduce their attack surface.
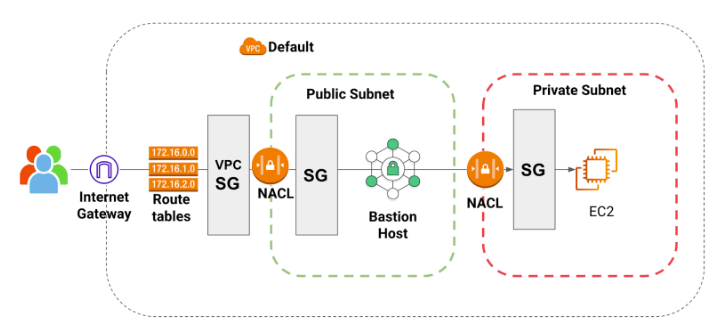
Think about it as a proxy, if your bastion is compromised, you can take immediate actions and your private network might not be impacted at all.
The routing between public and private subnets is managed using the NACL.
There are two types of bastion hosts you can implement:
- Nat Instances/Gateways
- Load Balancers
Connecting different VPCs
So far, we have seen how to connect from the web to your VPC public and private subnets, but if we think about different network topologies, there might be some scenarios where you would have different VPCs in your AWS environment and would like to connect between them. In order to do that you can use VPC Peering.
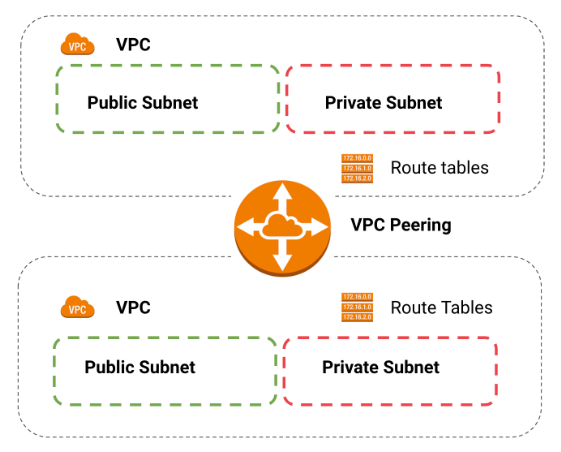
- VPC peering is a networking connection between two VPCs that enables you to route traffic between them using private IPv4 addresses or IPv6 addresses.
Keep in mind that this is a peer connection, therefore if you have 3 VPC you will need 2 VPC peerings.
For configuring the peering you need the VPC IDs and this will add new addresses into your route tables.
But what happens when we have multiple VPCs, multiple Peering and external connections, is that things can get really complicated. The solution for that are the Transit Gateways.
- A Transit Gateway is a network transit hub that you can use to interconnect your virtual private clouds (VPCs) and on-premises networks. As your cloud infrastructure expands globally, inter-Region peering connects transit gateways together using the AWS Global Infrastructure.
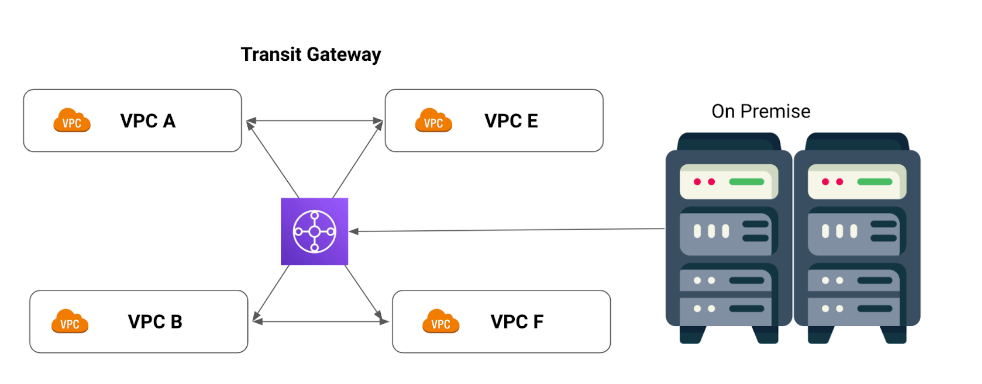
Pay special attention to this picture where we are also able to connect with On Premise. Let’s take a closer look at connecting on Premise servers and what things we might need.
Connecting your VPC with On-Premise servers
There might be a lot of scenarios where a Hybrid model between the cloud and your own servers is needed. There are different things we need to consider for being able to connect. Let’s have a look!
Direct Connect
Direct Connect provides Amazon Web Services (AWS) customers with a way to transfer data that does not involve using the public Internet. According to Amazon, private network connections provide a safer, more consistent network experience than Internet-based connections.
*Be careful cause it takes about a month to be provisioned and is not available in all locations.
Site to site VPN
A site-to-site virtual private network (VPN) is a connection between two or more networks, such as a corporate network and a branch office network. Many organizations use site-to-site VPNs to leverage an internet connection for private traffic as an alternative to using private MPLS circuits.
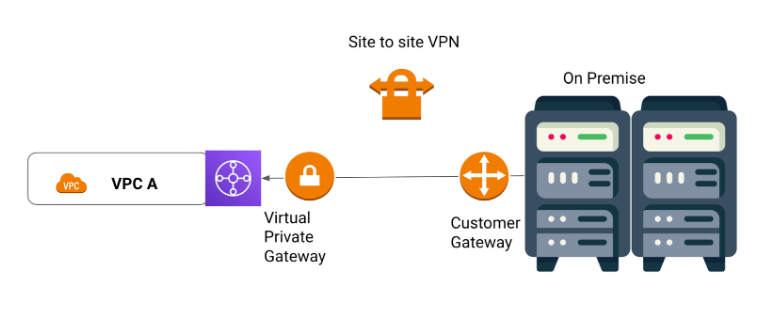
If your case requires a site to site VPN there are 2 concepts you need to know.
Virtual private gateway: A virtual private gateway is the VPN endpoint on the Amazon side of your Site-to-Site VPN connection that can be attached to a single VPC.
Customer gateway: A customer gateway is a resource that you create in AWS that represents the customer gateway device in your on-premises network.
VPC Endpoints
A VPC endpoint is a virtual device which is horizontally scaled, redundant and highly available, that provides communication between EC2 instances within your Virtual Private Cloud and other supported AWS services without introducing availability risks or bandwidth constraints on your network traffic.
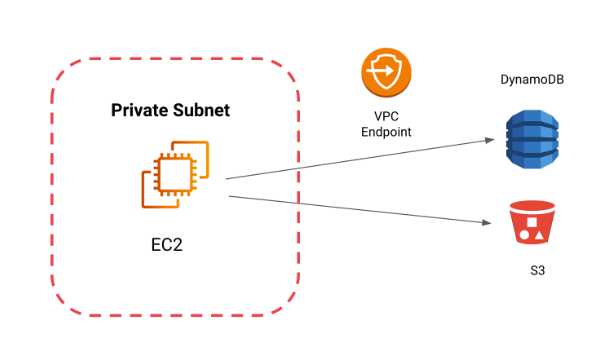
As today you can use VPC endpoints to connect your private instances directly with DynamoDB or S3.
One thing to keep in mind: AWS Private Link is not the same as the VPC endpoints.
Remember the VPC endpoint is the entry point in your VPC that enables you to connect privately to a service, while AWS PrivateLink is a technology that provides private connectivity between VPCs and services.
In other words, the VPC endpoint uses a Private Link for the connection.
Monitoring and support
VPC Flow logs
They help you track and understand traffic to and from your VPC, a subnet, or a network interface. This data is then stored in Amazon CloudWatch to analyze later.
VPC Reachability Analyzer
It is a configuration analysis tool that enables you to perform connectivity testing between a source resource and a destination resource in your virtual private clouds (VPCs). When the destination is reachable, Reachability Analyzer produces hop-by-hop details of the virtual network path between the source and the destination. When the destination is not reachable, Reachability Analyzer identifies the blocking component.
That was too much for VPC!
Take a moment to review these concepts and play around on the AWS console.
If you have any questions, need expert guidance, or want to explore further, feel free to reach out to us here


